red exploit corner the hidden danger in your cybersecurity Hacker attack computer hardware microchip while process data through ...
If you are searching about Abstract, warning, and warning triangle symbols Binary red background you've visit to the right page. We have 25 Pics about Abstract, warning, and warning triangle symbols Binary red background like Why is Reds Exploit Corner in 2025 the ultimate exploit hub?, Hacker attack computer hardware microchip while process data through and also Abstract, warning, and warning triangle symbols Binary red background. Here it is:
Abstract, Warning, And Warning Triangle Symbols Binary Red Background
 www.vecteezy.com
www.vecteezy.com
Abstract, warning, and warning triangle symbols Binary red background ...
What Is Exploit And How To Protect Your Computer?
 www.wallarm.com
www.wallarm.com
What is Exploit and How to Protect Your Computer?
Exploit Alert On A Red Binary Danger Background Stock Photo - Alamy
 www.alamy.com
www.alamy.com
Exploit Alert on a Red Binary Danger Background Stock Photo - Alamy
Cybersecurity 2.0 - DHL - Japan
 www.dhl.com
www.dhl.com
Cybersecurity 2.0 - DHL - Japan
Why Is Reds Exploit Corner In 2025 The Ultimate Exploit Hub?
 mymagazine.blog
mymagazine.blog
Why is Reds Exploit Corner in 2025 the ultimate exploit hub?
Cybersecurity Threat Abstract Red Binary Code Background Depicting
 pngtree.com
pngtree.com
Cybersecurity Threat Abstract Red Binary Code Background Depicting ...
Zero-Day Exploits: The Hidden Threats Of Cybersecurity - Tuned Into
 www.tunedsecurity.com
www.tunedsecurity.com
Zero-Day Exploits: The Hidden Threats of Cybersecurity - Tuned into ...
What Is A Zero-Day Exploit? And Why Are They Dangerous?
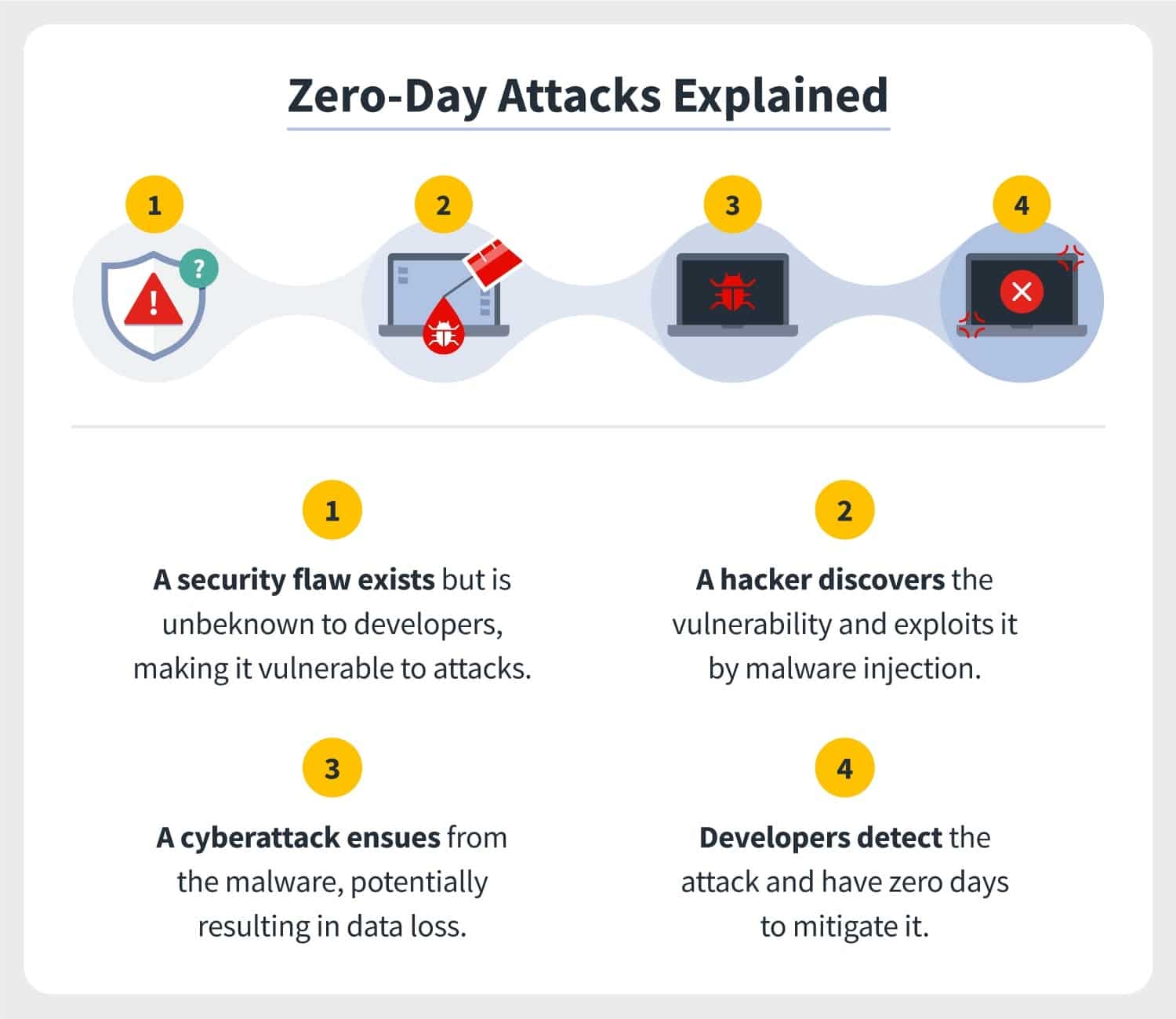 kinsta.com
kinsta.com
What Is a Zero-Day Exploit? And Why Are They Dangerous?
Why Is Reds Exploit Corner In 2025 The Ultimate Exploit Hub?
 mymagazine.blog
mymagazine.blog
Why is Reds Exploit Corner in 2025 the ultimate exploit hub?
10 Different Types Of Cyber Attacks & How To Recognize Them - InfoSec
 sectigostore.com
sectigostore.com
10 Different Types of Cyber Attacks & How To Recognize Them - InfoSec ...
AABGM Inc. On LinkedIn: Zero-Day Exploits: The Hidden Danger In The
 www.linkedin.com
www.linkedin.com
AABGM Inc. on LinkedIn: Zero-Day Exploits: The Hidden Danger In the ...
Concept Of Destroyed Cyber Security Design.Padlock Red Open On Dark Red
 stock.adobe.com
stock.adobe.com
Concept of destroyed cyber security design.Padlock red open on dark red ...
Exploit Security Warning On Red Binary Technology Background Stock
 www.alamy.com
www.alamy.com
Exploit Security Warning on Red Binary Technology Background Stock ...
Hacker Attack Computer Hardware Microchip While Process Data Through
 www.everypixel.com
www.everypixel.com
Hacker attack computer hardware microchip while process data through ...
Understanding Malware: What You Need To Know
 forestvpn.com
forestvpn.com
Understanding Malware: What You Need to Know
Premium Vector | A Vivid Digital Illustration Depicting A Cyber Attack
 www.freepik.com
www.freepik.com
Premium Vector | A vivid digital illustration depicting a cyber attack ...
Cyber Security Concept. A Red Danger Symbol With Glowing Glyphs And
 stock.adobe.com
stock.adobe.com
Cyber security concept. A red danger symbol with glowing glyphs and ...
Zero-Day Attacks: Understanding The Hidden Threat
 safe-connect.com
safe-connect.com
Zero-Day Attacks: Understanding the Hidden Threat
Padlock Inside Red Glowing Cyber Network Danger Of Cyber Attacks
 www.freepik.com
www.freepik.com
Padlock inside red glowing cyber network danger of cyber attacks ...
Ransomware Alert Message, Dark Red Screen, Highlighting Danger Of Cyber
 stock.adobe.com
stock.adobe.com
Ransomware alert message, dark red screen, highlighting danger of cyber ...
Don’t Let Cybersecurity Exploits Threaten Your Customer Experience
 www.linkedin.com
www.linkedin.com
Don’t let cybersecurity exploits threaten your customer experience
Padlock Inside Red Glowing Cyber Network. Danger Of Cyber Attacks
 www.dreamstime.com
www.dreamstime.com
Padlock Inside Red Glowing Cyber Network. Danger of Cyber Attacks ...
Cyber Security Destroyed.Padlock Red Open On Electric Circuits Network
 stock.adobe.com
stock.adobe.com
Cyber security destroyed.Padlock red open on electric circuits network ...
Concept Of Destroyed Cyber Security.Padlock Red Open On Electric
 stock.adobe.com
stock.adobe.com
Concept of destroyed cyber security.Padlock red open on electric ...
Premium Photo | Scary Hacker Illustration Cyber Security Technology
 www.freepik.com
www.freepik.com
Premium Photo | Scary hacker illustration cyber security technology ...
Cyber security concept. a red danger symbol with glowing glyphs and. Premium vector. Abstract, warning, and warning triangle symbols binary red background